OIC Connectivity Agent
The OIC connectivity agent is the answer for a secure hybrid deployment, where you have a mix of cloud and on-premise applications and need to ensure a secure communication.
The agent is the handler/listener that manages both inbound/outbound communication. This ensures that there is no need to open a port in the on premise firewall.
Fortunately Mordac is not a Product Manager for OIC:)
The agent group is a logical group to which we can associate the physical agents installed on premise. Very simple to create one - Just provide a name and a description.
On the same place where you created the agent group, download the connectivity agent.
Let's stop for a second and look to the System Requirements!
The agent is only certified with Oracle JDK Version 8.
The agent is certified on the following operating systems:
Oracle Enterprise Linux 6.x
Oracle Enterprise Linux 7.2
Oracle Enterprise Linux 7.5
RedHat Enterprise Linux 6.6
RedHat Enterprise Linux 7.2
RedHat Enterprise Linux 7.5
RedHat Enterprise Linux 7.6
Suse Linux Enterprise Edition 12 SP2
Windows Standard Edition 2016
Oracle Enterprise Linux 7.2
Oracle Enterprise Linux 7.5
RedHat Enterprise Linux 6.6
RedHat Enterprise Linux 7.2
RedHat Enterprise Linux 7.5
RedHat Enterprise Linux 7.6
Suse Linux Enterprise Edition 12 SP2
Windows Standard Edition 2016
Windows 2019
Whether the installation is on Windows or Linux, the process is pretty much the same. The next steps illustrate the Linux installation.
The main file to configure is InstallerProfile.cfg
# Required Parameters
# oic_URL format should be https://hostname:sslPort
oic_URL=https://oic_host:ssl_port
agent_GROUP_IDENTIFIER=
#Optional Parameters
oic_USER=
oic_PASSWORD=
#Proxy Parameters
proxy_HOST=
proxy_PORT=
proxy_USER=
proxy_PASSWORD=
proxy_NON_PROXY_HOSTS=
oic_URL is the HTTPS URL for the Oracle Integration host.
agent_GROUP_IDENTIFIER - the identifier for the agent group created in the previous step.
oic_user and oic_password - if left empty it will ask for credentials when initializing the agent.You can type your credentials in the file, and it will be encrypted once it runs the first time
proxy parameters are needed in case of an on-premise proxy.
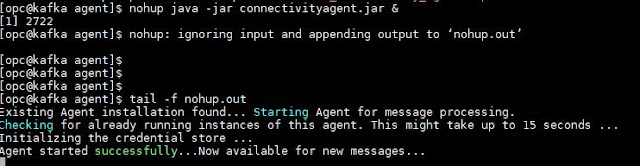
Once the configuration file is complete, the agent is ready to be started.
java –jar connectivityagent.jarAll of these steps (and more) can be found here!
nohup java -jar connectivity.jar &Note: This is only valid for Linux. At the moment it's not possible to run the agent as a service in Windows.
The monitoring menu offers also an Agent view where you can have the full visibility to all the Agents status.
There are many more topics to cover, as the high availability setup, agent upgrade, performance tuning etc. I will address this in upcoming posts. Stay tuned....





Comments
Post a Comment